Ieee 802.1x Cheat Sheet
ADVERTISEMENT
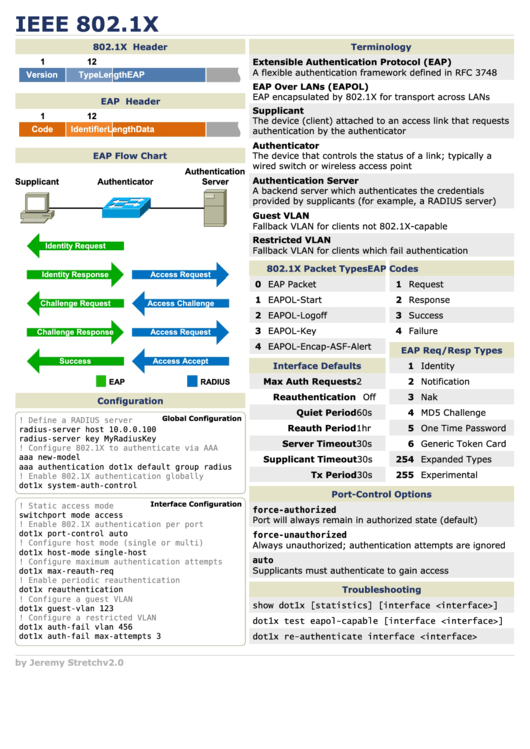
IEEE 802.1X
packetlife.net
802.1X Header
Terminology
1
1
2
Extensible Authentication Protocol (EAP)
A flexible authentication framework defined in RFC 3748
Version
Type
Length
EAP
EAP Over LANs (EAPOL)
EAP encapsulated by 802.1X for transport across LANs
EAP Header
Supplicant
1
1
2
The device (client) attached to an access link that requests
Code
Identifier
Length
Data
authentication by the authenticator
Authenticator
EAP Flow Chart
The device that controls the status of a link; typically a
wired switch or wireless access point
Authentication
Authentication Server
Supplicant
Authenticator
Server
A backend server which authenticates the credentials
provided by supplicants (for example, a RADIUS server)
Guest VLAN
Fallback VLAN for clients not 802.1X-capable
Restricted VLAN
Identity Request
Fallback VLAN for clients which fail authentication
802.1X Packet Types
EAP Codes
Identity Response
Access Request
0 EAP Packet
1 Request
1 EAPOL-Start
2 Response
Challenge Request
Access Challenge
2 EAPOL-Logoff
3 Success
3 EAPOL-Key
4 Failure
Challenge Response
Access Request
4 EAPOL-Encap-ASF-Alert
EAP Req/Resp Types
Success
Access Accept
Interface Defaults
1 Identity
Max Auth Requests 2
2 Notification
EAP
RADIUS
Reauthentication Off
3 Nak
Configuration
Quiet Period 60s
4 MD5 Challenge
Global Configuration
! Define a RADIUS server
Reauth Period 1hr
5 One Time Password
radius-server host 10.0.0.100
radius-server key MyRadiusKey
Server Timeout 30s
6 Generic Token Card
! Configure 802.1X to authenticate via AAA
aaa new-model
Supplicant Timeout 30s
254 Expanded Types
aaa authentication dot1x default group radius
Tx Period 30s
255 Experimental
! Enable 802.1X authentication globally
dot1x system-auth-control
Port-Control Options
Interface Configuration
! Static access mode
force-authorized
switchport mode access
Port will always remain in authorized state (default)
! Enable 802.1X authentication per port
dot1x port-control auto
force-unauthorized
! Configure host mode (single or multi)
Always unauthorized; authentication attempts are ignored
dot1x host-mode single-host
auto
! Configure maximum authentication attempts
Supplicants must authenticate to gain access
dot1x max-reauth-req
! Enable periodic reauthentication
Troubleshooting
dot1x reauthentication
! Configure a guest VLAN
show dot1x [statistics] [interface <interface>]
dot1x guest-vlan 123
! Configure a restricted VLAN
dot1x test eapol-capable [interface <interface>]
dot1x auth-fail vlan 456
dot1x re-authenticate interface <interface>
dot1x auth-fail max-attempts 3
by Jeremy Stretch
v2.0
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1