Sqlmap Cheatsheet 1.0
ADVERTISEMENT
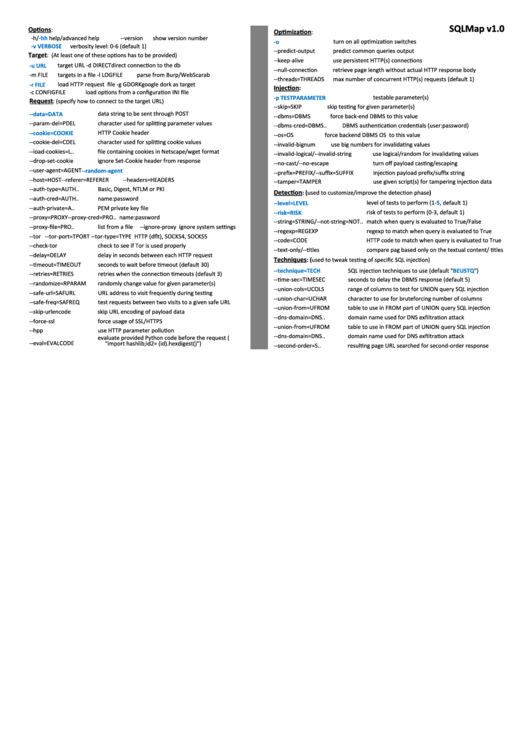
SQLMap v1.0
Options
:
Optimization
:
-h/-hh
help/advanced help
--version
show version number
turn on all optimization switches
-o
-v VERBOSE
verbosity level: 0-6 (default 1)
--predict-output
predict common queries output
Target
: (At least one of these options has to be provided)
--keep-alive
use persistent HTTP(s) connections
target URL
-d DIRECT
direct connection to the db
-u URL
--null-connection
retrieve page length without actual HTTP response body
-m FILE
targets in a file
-l LOGFILE
parse from Burp/WebScarab
--threads=THREADS
max number of concurrent HTTP(s) requests (default 1)
load HTTP request file
-g GDORK
google dork as target
-r FILE
Injection
:
-c CONFIGFILE
load options from a configuration INI file
-p TESTPARAMETER
testable parameter(s)
Request
: (specify how to connect to the target URL)
--skip=SKIP
skip testing for given parameter(s)
--data=DATA
data string to be sent through POST
--dbms=DBMS
force back-end DBMS to this value
--param-del=PDEL
character used for splitting parameter values
--dbms-cred=DBMS..
DBMS authentication credentials (user:password)
HTTP Cookie header
--cookie=COOKIE
--os=OS
force backend DBMS OS to this value
--cookie-del=CDEL
character used for splitting cookie values
--invalid-bignum
use big numbers for invalidating values
--load-cookies=L..
file containing cookies in Netscape/wget format
--invalid-logical/--invalid-string
use logical/random for invalidating values
--drop-set-cookie
ignore Set-Cookie header from response
--no-cast/--no-escape
turn off payload casting/escaping
--user-agent=AGENT
--random-agent
--prefix=PREFIX/--suffix=SUFFIX
injection payload prefix/suffix string
--host=HOST
--referer=REFERER
--headers=HEADERS
--tamper=TAMPER
use given script(s) for tampering injection data
--auth-type=AUTH..
Basic, Digest, NTLM or PKI
Detection
: (used to customize/improve the detection phase)
--auth-cred=AUTH..
name:password
level of tests to perform (1-5, default 1)
--level=LEVEL
--auth-private=A..
PEM private key file
risk of tests to perform (0-3, default 1)
--risk=RISK
--proxy=PROXY
--proxy-cred=PRO.. name:password
--string=STRING/--not-string=NOT.. match when query is evaluated to True/False
--proxy-file=PRO..
list from a file
--ignore-proxy ignore system settings
--regexp=REGEXP
regexp to match when query is evaluated to True
--tor --tor-port=TPORT
--tor-type=TYPE HTTP (dflt), SOCKS4, SOCKS5
--code=CODE
HTTP code to match when query is evaluated to True
--check-tor
check to see if Tor is used properly
--text-only/--titles
compare pag based only on the textual content/ titles
--delay=DELAY
delay in seconds between each HTTP request
Techniques
: (used to tweak testing of specific SQL injection)
--timeout=TIMEOUT
seconds to wait before timeout (default 30)
--technique=TECH
SQL injection techniques to use (default "BEUSTQ")
--retries=RETRIES
retries when the connection timeouts (default 3)
--time-sec=TIMESEC
seconds to delay the DBMS response (default 5)
--randomize=RPARAM
randomly change value for given parameter(s)
--union-cols=UCOLS
range of columns to test for UNION query SQL injection
--safe-url=SAFURL
URL address to visit frequently during testing
--union-char=UCHAR
character to use for bruteforcing number of columns
--safe-freq=SAFREQ
test requests between two visits to a given safe URL
--union-from=UFROM
table to use in FROM part of UNION query SQL injection
--skip-urlencode
skip URL encoding of payload data
--dns-domain=DNS..
domain name used for DNS exfiltration attack
--force-ssl
force usage of SSL/HTTPS
--union-from=UFROM
table to use in FROM part of UNION query SQL injection
--hpp
use HTTP parameter pollution
--dns-domain=DNS..
domain name used for DNS exfiltration attack
evaluate provided Python code before the request (e.g.
--eval=EVALCODE
"import hashlib;id2=hashlib.md5(id).hexdigest()")
--second-order=S..
resulting page URL searched for second-order response
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1 2
2








