Cissp & Security+ Cheat Sheet
ADVERTISEMENT
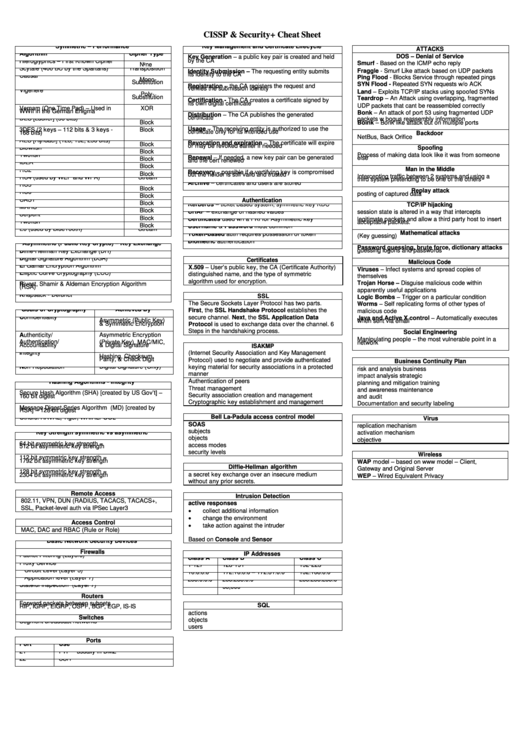
CISSP & Security+ Cheat Sheet
Symmetric – Performance
ATTACKS
Key Management and Certificate Lifecycle
DOS – Denial of Service
Key Generation – a public key pair is created and held
Algorithm
Cipher Type
Hieroglyphics – First Known Cipher
Smurf - Based on the ICMP echo reply
by the CA
None
Identity Submission – The requesting entity submits
Fraggle - Smurf Like attack based on UDP packets
Scytale (400 BC by the Spartans)
Transposition
Ping Flood - Blocks Service through repeated pings
its identity to the CA
Caesar
Mono-
SYN Flood - Repeated SYN requests w/o ACK
Registration – the CA registers the request and
Substitution
Land – Exploits TCP/IP stacks using spoofed SYNs
verifies the submission identity
Vigenere
Poly-
Teardrop – An Attack using overlapping, fragmented
Certification - The CA creates a certificate signed by
Substitution
UDP packets that cant be reassembled correctly
Vernam (One Time Pad) – Used in
its own digital certificate
XOR
Bonk – An attack of port 53 using fragmented UDP
Distribution – The CA publishes the generated
WWII in the German Enigma
packets w bogus reassembly information
certificate
DES [Lucifer] (56 bits)
Block
Boink – Bonk like attack but on multiple ports
Usage – The receiving entity is authorized to use the
3DES (2 keys – 112 bits & 3 keys -
Block
Backdoor
certificate only for its intended use
168 bits)
NetBus, Back Orifice
Revocation and expiration – The certificate will expire
AES [Rijndael] (128, 192, 256 bits)
Block
Spoofing
or may be revoked earlier if needed
Blowfish
Block
Process of making data look like it was from someone
Renewal – If needed, a new key pair can be generated
Twofish
Block
else
and the cert renewed
IDEA
Block
Man in the Middle
Recovery – possible if a vertifying key is compromised
RC2
Block
Intercepting traffic between 2 systems and using a
but the holder is still valid and trusted
RC4 (used by W EP and WPA)
Stream
third system pretending to be one of the others
Archive – certificates and users are stored
RC5
Block
Replay attack
RC6
Block
posting of captured data
Authentication
CAST
Block
TCP/IP hijacking
Kerberos – ticket based system, symmetric key KDC
MARS
Block
session state is altered in a way that intercepts
CHAP – exchange of hashed values
Serpent
Block
legitimate packets and allow a third party host to insert
Certificates used w/I a PKI for Asymmetric key
Twofish
Block
acceptable packets.
Username & Password most common
E0 (used by BlueTooth)
Stream
Mathematical attacks
Token-based auth requires possession of token
(Key guessing)
Biometric authentication
Asymmetric (Public Key Crypto) – Key Exchange
Password guessing, brute force, dictionary attacks
Diffie-Hellman Key Exchange (DH)
guessing logons and passwords
Certificates
Digital Signature Algorithm (DSA)
Malicious Code
X.509 – User’s public key, the CA (Certificate Authority)
Viruses – Infect systems and spread copies of
El Gamal Encryption Algorithm
distinguished name, and the type of symmetric
themselves
Elliptic Curve Cryptography (ECC)
algorithm used for encryption.
Trojan Horse – Disguise malicious code within
Rivest, Shamir & Aldeman Encryption Algorithm
apparently useful applications
(RSA)
SSL
Logic Bombs – Trigger on a particular condition
Knapsack - Defunct
Worms – Self replicating forms of other types of
The Secure Sockets Layer Protocol has two parts.
First, the SSL Handshake Protocol establishes the
malicious code
Goals of Cryptography
Achieved By
Java and Active X control – Automatically executes
secure channel. Next, the SSL Application Data
Confidentiality
Asymmetric (Public Key)
Protocol is used to exchange data over the channel. 6
when sent via email
& Symmetric Encryption
Steps in the handshaking process.
Social Engineering
Authenticity/
Asymmetric Encryption
Manipulating people – the most vulnerable point in a
Authentication/
(Private Key), MAC/MIC,
ISAKMP
network
Accountability
& Digital Signature
(Internet Security Association and Key Management
Integrity
Hashing, Checksum,
Protocol) used to negotiate and provide authenticated
Business Continuity Plan
Parity, & Check Digit
keying material for security associations in a protected
risk and analysis business
Non-Repudiation
Digital Signature (Only)
manner
impact analysis strategic
Authentication of peers
planning and mitigation training
Hashing Algorithms - Integrity
Threat management
and awareness maintenance
Secure Hash Algorithm (SHA) [created by US Gov’t] –
Security association creation and management
and audit
160 bit digest
Cryptographic key establishment and management
Documentation and security labeling
Message Digest Series Algorithm (MD) [created by
RSA] – 128 bit digest
Bell La-Padula access control model
Virus
Others: HAVAL, Tiger, W HIRLPOOL
SOAS
replication mechanism
subjects
activation mechanism
Key Strength symmetric vs asymmetric
objects
objective
64 bit symmetric key strength =
access modes
512 bit asymmetric key strength
security levels
Wireless
112 bit symmetric key strength =
WAP model – based on www model – Client,
1792 bit asymmetric key strength
Diffie-Hellman algorithm
Gateway and Original Server
128 bit symmetric key strength =
a secret key exchange over an insecure medium
WEP – W ired Equivalent Privacy
2304 bit asymmetric key strength
without any prior secrets.
Remote Access
Intrusion Detection
802.11, VPN, DUN (RADIUS, TACACS, TACACS+,
active responses
SSL, Packet-level auth via IPSec Layer3
collect additional information
change the environment
Access Control
take action against the intruder
MAC, DAC and RBAC (Rule or Role)
Based on Console and Sensor
Basic Network Security Devices
Firewalls
IP Addresses
Packet Filtering (Layer3)
Class A
Class B
Class C
Proxy Service
1-127
128-191
192-223
Circuit Level (Layer 3)
172.16.0.0 – 172.31.0.0
10.0.0.0
192.168.0.0
Application level (Layer 7)
255.0.0.0
255.255.0.0
255.255.255.0
Stateful Inspection (Layer 7)
65,000
Routers
Forward packets between subnets
SQL
RIP, IGRP, EIGRP, OSPF, BGP, EGP, IS-IS
actions
Switches
objects
Segment broadcast networks
users
Ports
Port
Use
FTP – usually in DMZ
21
22
SSH
ADVERTISEMENT
0 votes
Related Articles
Related forms
Related Categories
Parent category: Education
 1
1 2
2 3
3